Customers who have deployed Meraki MX cloud-managed routers have really benefited from its ability to centrally manage secure multi-site networks. Using built-in site-to-site VPN capability and the link aggregation and failover of the MX70, secure multi-site networks can be deployed while reducing configuration complexity and lowering branch connectivity costs. This is best illustrated through a few examples, so part of Meraki’s network configuration is shown below.
Deploying a site-to-site VPN network
Ordinarily, configuring a multi-site VPN mesh network can be complex and tedious. Site-to-site networks need to be established with WAN routes for each peer-to-peer connection, and IPsec needs to be configured. That includes setting up authentication, security association parameters, and possibly manual exchange of keys (or configuration of a key management protocol).Deploying MX routers into a multi-site networks eliminates the tedious manual configuration of the site-to-site VPN. Adding a site into the network’s architecture is done simply by adding the MX router into the organization, setting the local subnet, and enabling participation in the VPN. The MX routers automatically discover each other through Meraki’s cloud network so you don’t have to manually enable routes between each. Figure 1 shows the high level configuration of a typical multi-site network (only three sites are shown for simplicity).
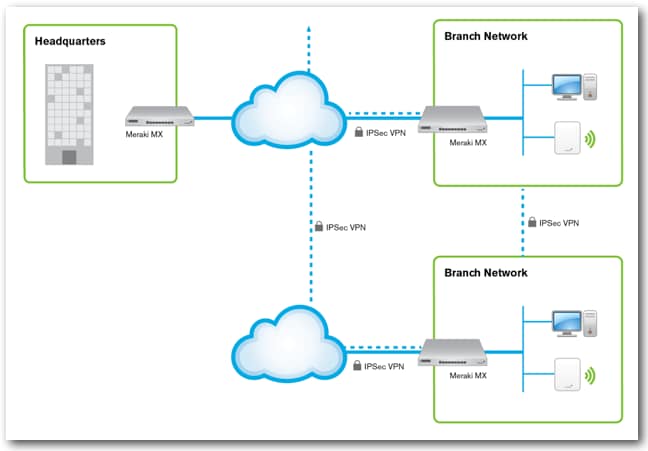
Figure 1: Meraki MX deployment architecture
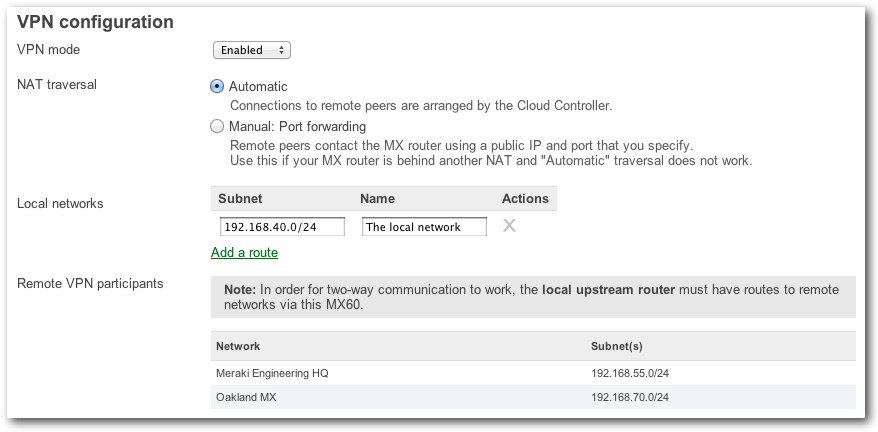
Figure 2: Burlingame MX VPN configuration
The configuration of the Burlingame MX is straightforward, and its 192.168.40.0/24 subnet appears at Meraki’s engineering HQ MX. The engineering HQ MX sits in Meraki’s San Francisco headquarters, and its network has several VLANs that can be selectively included in the site-to-site VPN and made available to the peers on the network. An organization-wide site-to-site firewall can enforce complex custom policies, such as limiting selected traffic between certain sites.
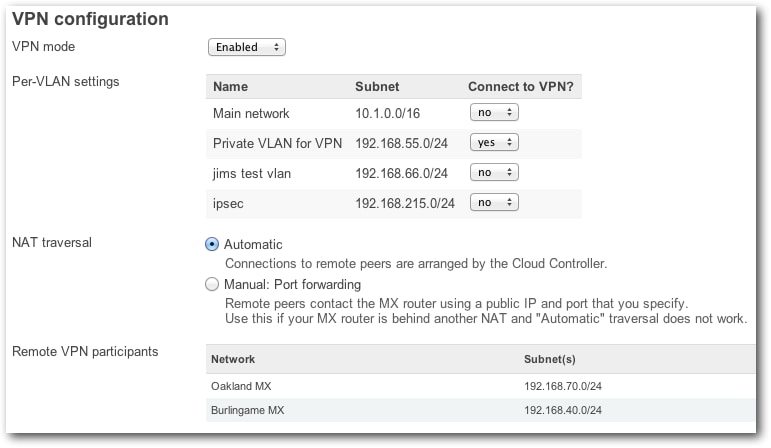
Figure 3: Engineering HQ MX VPN Configuration

No comments:
Post a Comment